Back
Jan 28, 2026
EDAMAME Agents 1.0: User-Up Security, Finally Unlocked Through AI

Frank Lyonnet

EDAMAME didn’t arrive at version 1.0 by accident.
From the very beginning, this was the system we intended to build. The reason it took time is not because the vision changed, but because the missing piece had to arrive first.
We started EDAMAME at the same moment it became obvious that AI would fundamentally change how developers interact with complex systems. We were among the earliest users of tools like Cursor, and that experience mattered. It was the first clear signal that AI would not stop at autocomplete or suggestions, but would evolve into something closer to collaboration and reasoning.
From that moment, one thing became clear to us: user-up security would only be possible once AI was good enough to reason over real system state.
Traditional security posture is admin-down by design. Centralized teams define policies, push controls, lock machines, and hope developers comply. It works on paper, but in practice it creates friction, blind spots, and workarounds. Developers lose ownership of their machines, security teams lose trust in what’s actually running, and posture becomes something audited periodically instead of lived continuously.
Our conviction from day one was that posture needed to move in the opposite direction. Security had to start at the edge, with the user, and scale upward. That meant every developer, contractor, and system owner needed their own intelligent security agent—one that understands their machine, explains risks in context, and helps them act without waiting on centralized intervention.
But that model only works if the agent can reason, prioritize, and explain. Without AI, user-up security collapses into noise.
That insight shaped every architectural decision we made.
We built signal pipelines before assistants, agents before interfaces, and reversible actions before automation. We assumed AI would eventually be capable of real reasoning, and we made sure that when it was, the foundations underneath it would already be solid.
Today, with the launch of EDAMAME Agents 1.0, that system is complete.
EDAMAME Agents 1.0 brings together EDAMAME Security (the workstation and endpoint app) and EDAMAME Posture (the CLI for servers, CI, and headless environments) into a single, coherent security posture platform.
This is version 1.0 not because we ran out of ideas, but because the system has reached the shape it was designed to reach.
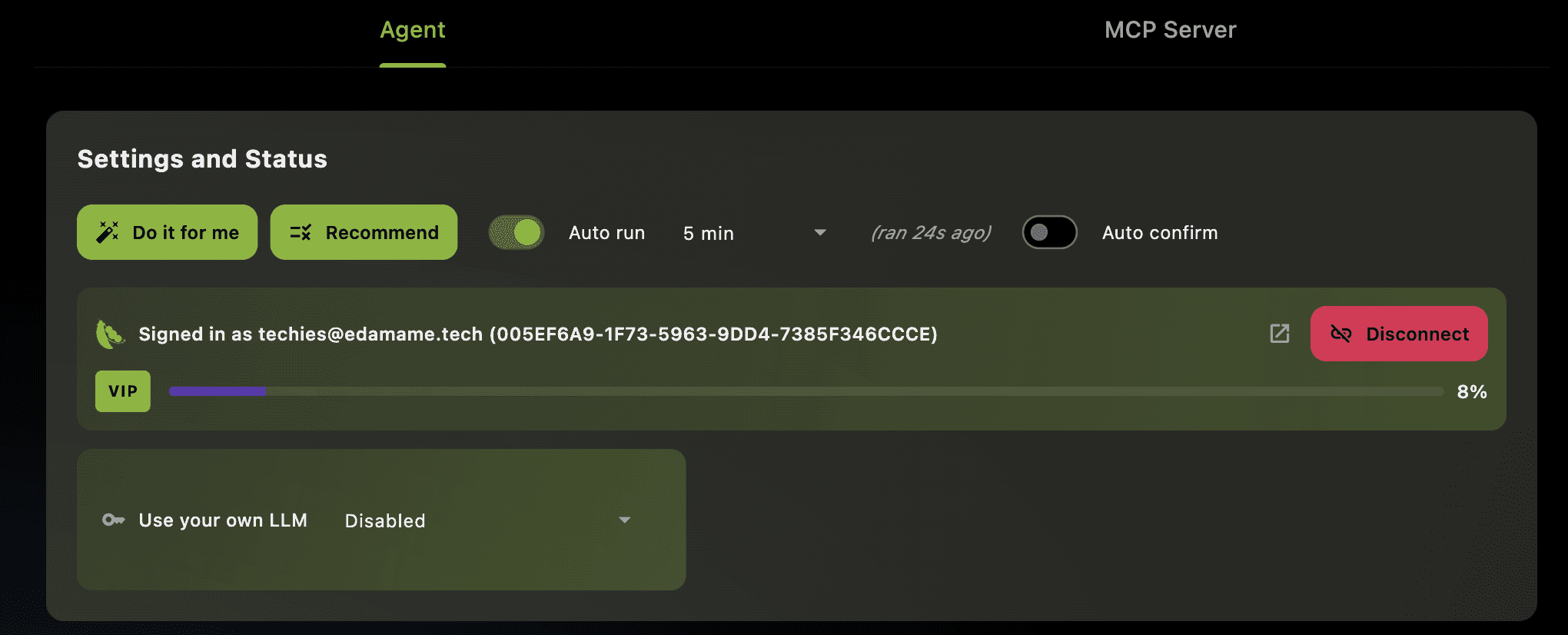
A System That Starts With Signal, Not AI
From day one, we were deliberate about where AI belongs.
EDAMAME does not start with a language model and ask it to guess what is wrong. It starts by collecting high-quality security signals across the system, the network, identity, and runtime behavior. Only after those signals are curated, correlated, and reduced into something meaningful do we involve AI.
That decision predates today’s LLM hype. We knew that without clean signal and strong context, AI would amplify noise instead of reducing it.
With portal.edamame.tech, that experience is now accessible without friction. You authenticate once, connect your machines, and from that point on EDAMAME Security can continuously reason about your posture, explain risks clearly, and help you decide what to do next. The built-in LLM subscription removes the final barrier, making the system usable out of the box without external dependencies.
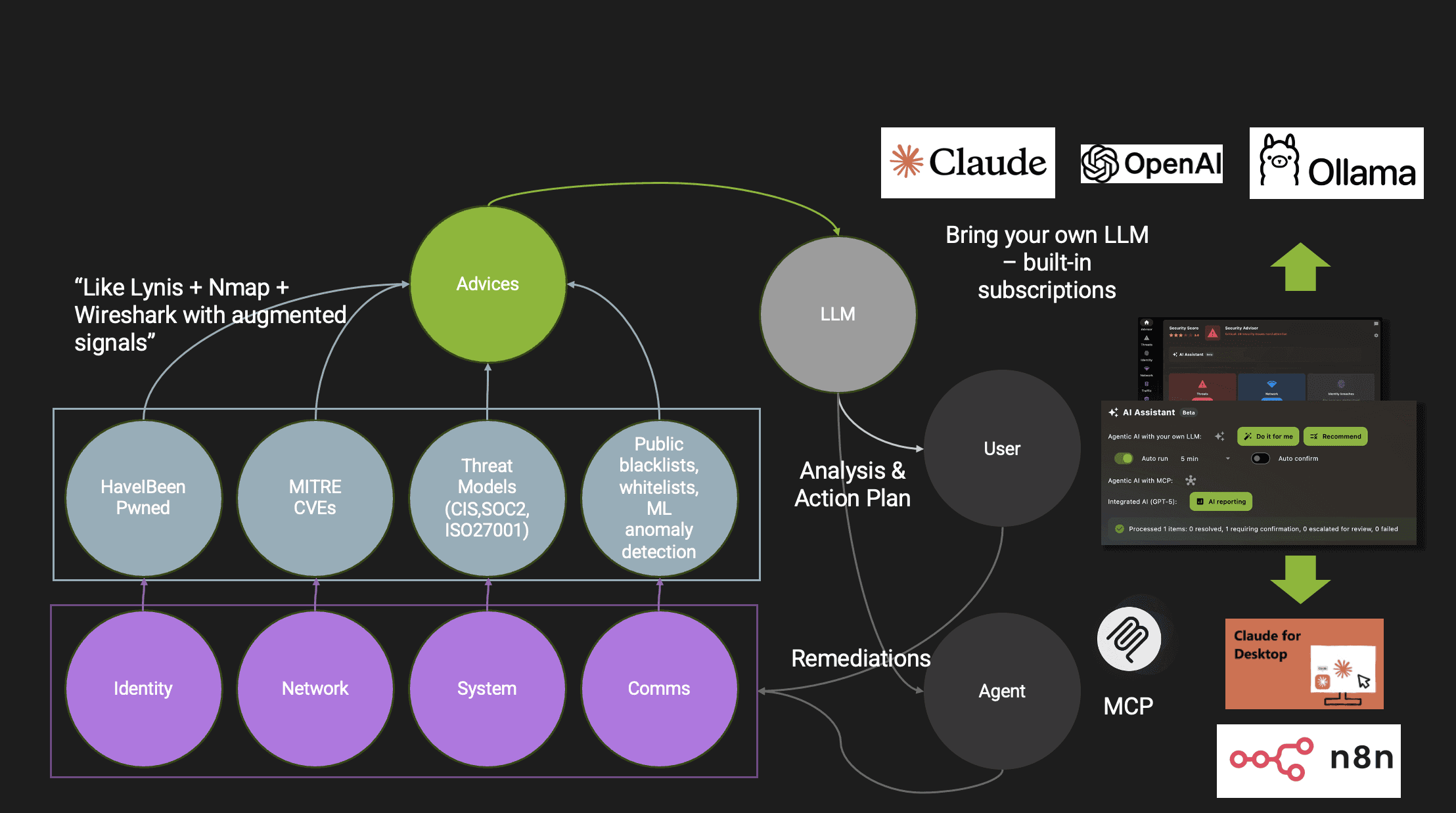
What User-Up Security Feels Like on a Workstation
On a workstation, EDAMAME Security integrates directly into the way developers already work. You install the app on Windows, macOS, or Linux, log in, and start analyzing.
Instead of overwhelming you with findings, the agent surfaces a small number of issues that genuinely deserve attention. It might notice that your primary email address appeared in a recent breach, that SSH or remote login is enabled on your laptop even though you rarely use it, that a new device appeared on your network with an unusual number of open ports, or that a background process is communicating with blacklisted infrastructure using a command-and-control-like traffic pattern.
What matters is not just detection, but interpretation.
The assistant explains why something is risky, how urgent it is, and what safe remediation looks like in your context. If an issue can be fixed automatically without risk, it offers to do so. If a change could have side effects, it asks before acting.
Every action is transparent, logged, and reversible. That constraint was intentional. Automation without reversibility is not assistance, it is risk. The result is not just a more secure machine, but a clearer understanding of why it is secure.
This is user-up security in practice: the person closest to the system remains in control, supported by an agent that understands both security and intent.
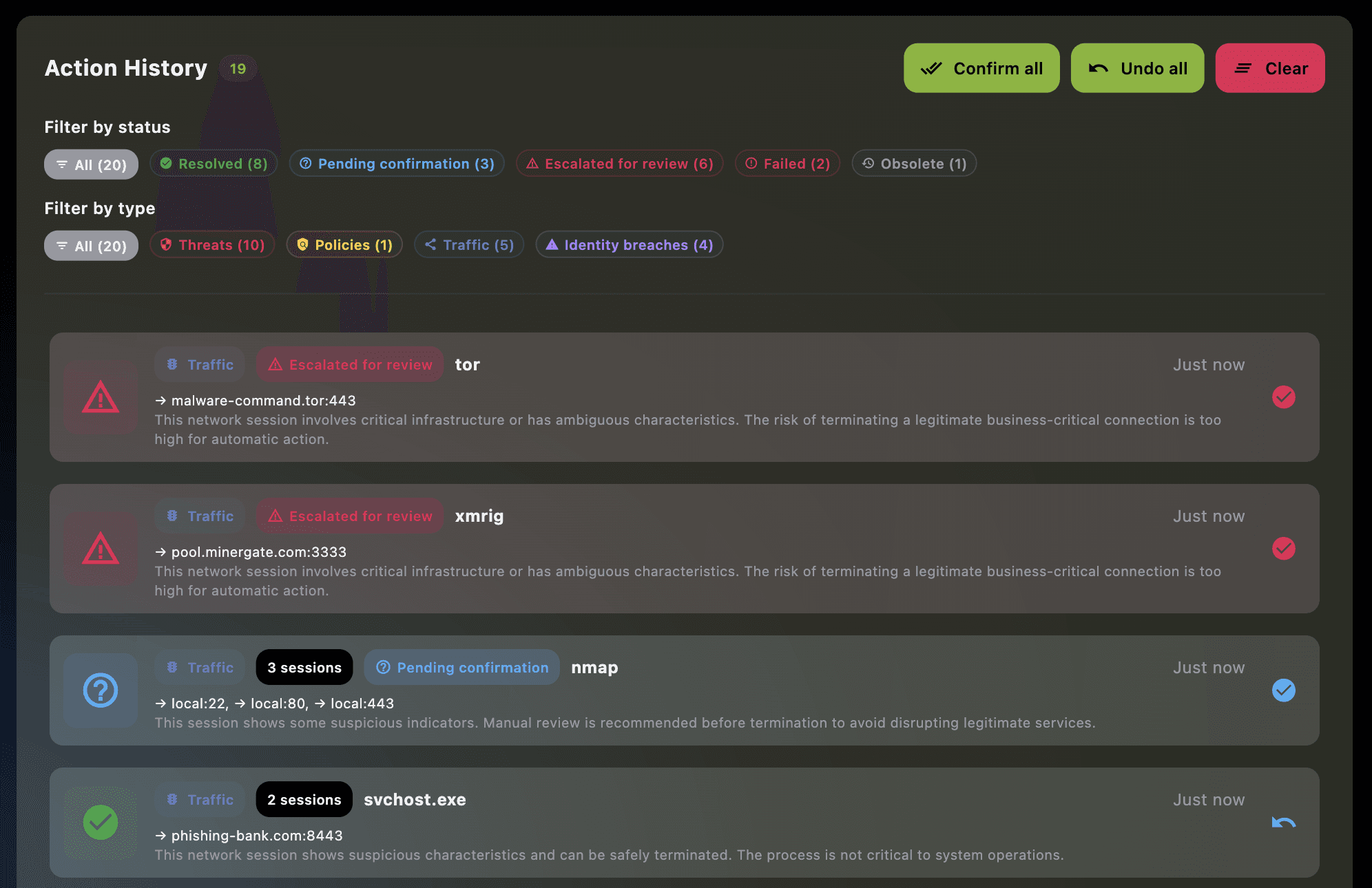
Servers, CI, and Human-in-the-Loop Escalation
Servers behave differently, and EDAMAME treats them differently by design.
For headless environments, EDAMAME Posture connects servers, build runners, and CI environments to the same posture engine. Authentication happens via an API key, and analysis runs continuously without requiring dashboards or UI access.
What completes the loop is communication.
Instead of pushing findings into another centralized console, EDAMAME Posture reports actions and decisions directly into a Slack channel. As the agent runs, it explains what it is doing, what it has fixed automatically, and where human confirmation is required.
If a remediation step requires judgment, EDAMAME does not guess. It escalates. The Slack channel becomes the shared interface where the system asks questions, records decisions, and keeps humans firmly in control.
In practice, this means catching weak password policies, outdated packages with known vulnerabilities, or services listening on exposed ports long before they become incidents. It also means posture management becomes continuous and conversational, not periodic and bureaucratic.
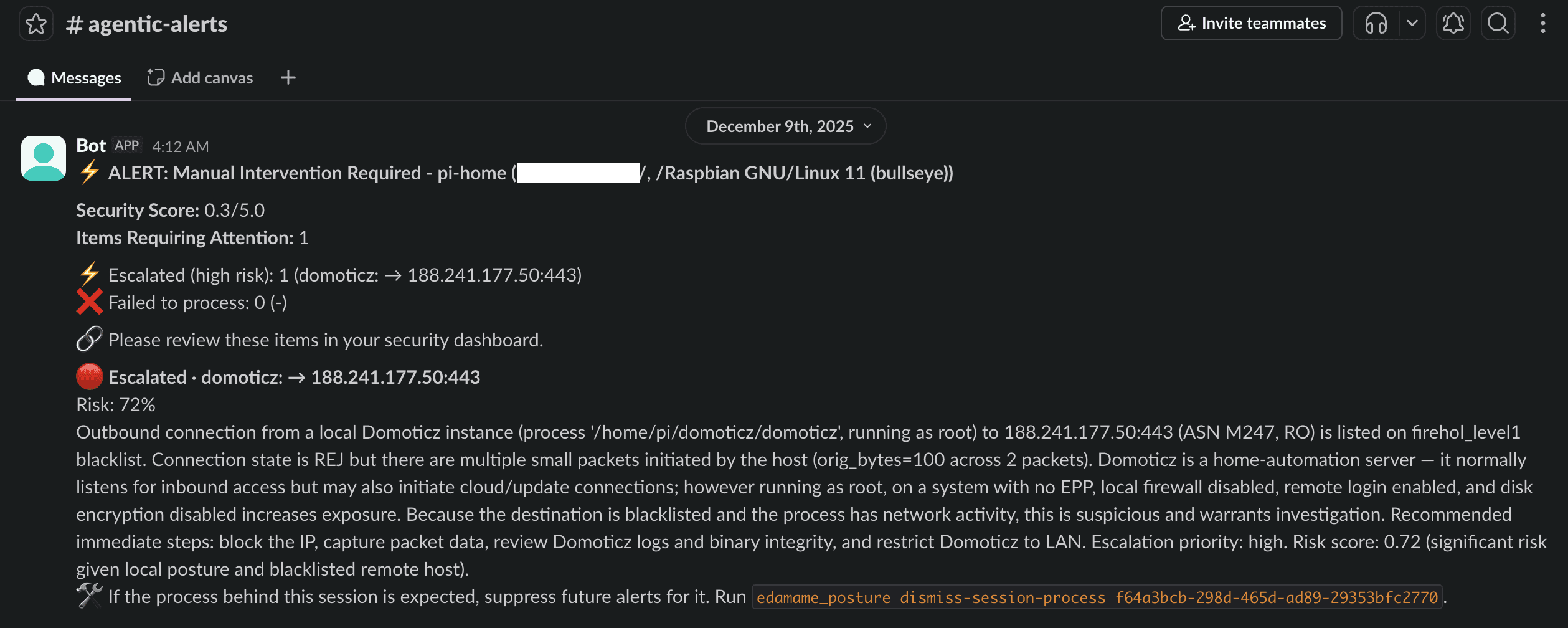
When Environments Become Dynamic
Static analysis answers whether a system is configured correctly. Dynamic analysis answers whether it is behaving correctly over time.
For exposed services and complex environments, EDAMAME Agents enable continuous traffic analysis. The agent observes which processes communicate, where they communicate, how often, and how those patterns evolve. That behavior is correlated with continuously updated blacklists and reputation data.
Outbound connections to known malicious infrastructure are flagged immediately, with attribution to the originating process. Beyond known threats, anomaly detection surfaces unexpected behavior, such as a normally silent process suddenly beaconing externally or traffic patterns diverging sharply from historical baselines.
When this happens, the assistant explains what changed, why it matters, and whether it aligns with known malicious behavior. In Slack-integrated environments, escalation happens where people already communicate, not in another security console.
Stability, Performance, and Readiness to Scale
Reaching 1.0 was not just about features.
A significant part of the work went into stability, performance, and user experience. Agents had to be predictable. Analysis had to feel fast and interactive. Fixes had to be safe, reversible, and clearly explained. The app had to stay out of the way, and the CLI had to behave like a serious system tool, not a demo.
That work is mostly invisible when done well, but it is what turns a promising idea into something people can rely on every day. We are genuinely proud of where EDAMAME Agents landed in terms of robustness and usability.
Open Foundations, Transparent by Design
EDAMAME Agents are built on open foundations. Core components are available on GitHub, including the EDAMAME Security engine and the EDAMAME Posture CLI. Transparency matters in security, and we believe trust is earned by design, not marketing.
You can get started across our repositories:
What 1.0 Means — and What Comes Next
EDAMAME Agents 1.0 is the point where the foundation is solid enough to scale without compromise.
Now that the architecture, UX, stability, and performance are where they need to be, our focus shifts to working closely with users to maximize real-world value. Real environments and real feedback are how this system gets sharper.
This is the system we set out to build when we realized AI would unlock user-up security. It is complete, stable, and ready.

Frank Lyonnet
Share this post