Tech Leaders
Endpoint Security That Unleashes Your Devs
Shift security to where work actually happens—at the device. EDAMAME’s AI assistant makes developers and contractors first‑response defenders, while posture‑based access and the Hub give you real‑time, audit‑ready assurance—with no remote device control required.
Features
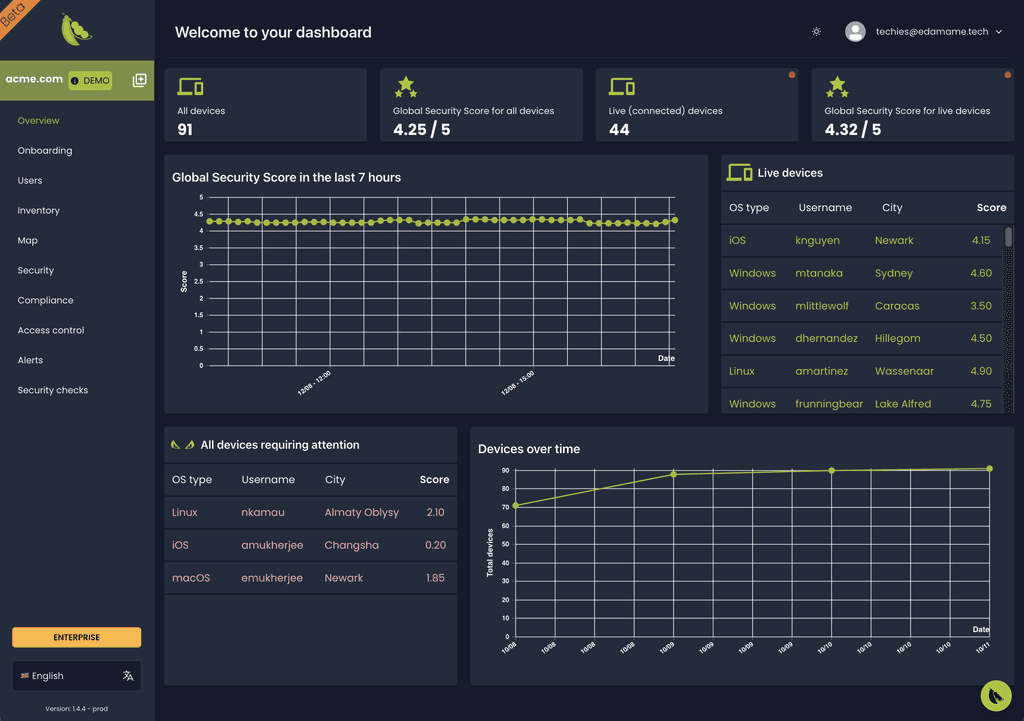
Holistic security for every endpoint
Our dashboard gives you unprecedented, holistic insight into the security posture of every endpoint in your SDLC—ensuring security and compliance without alienating developers.
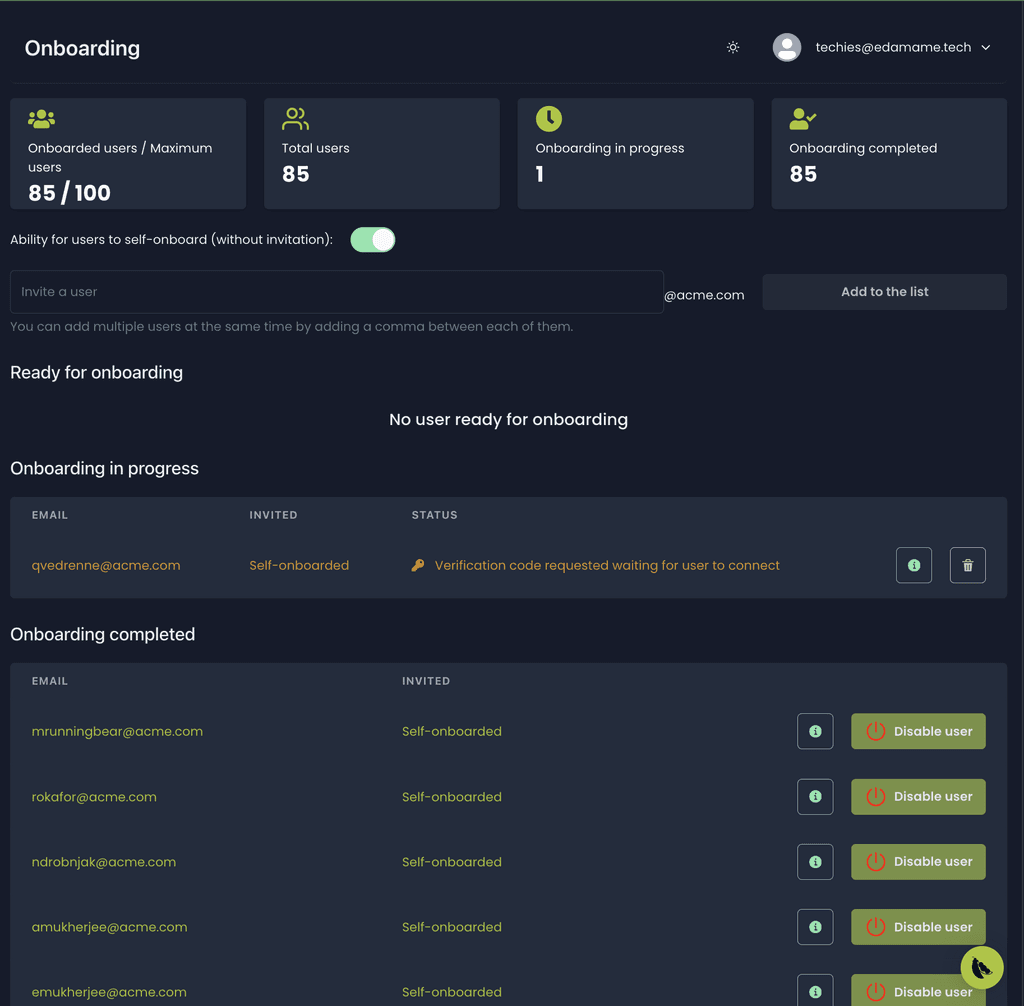
End-user onboarding
Manage the full lifecycle of users of your corporate resources—employees or contractors.
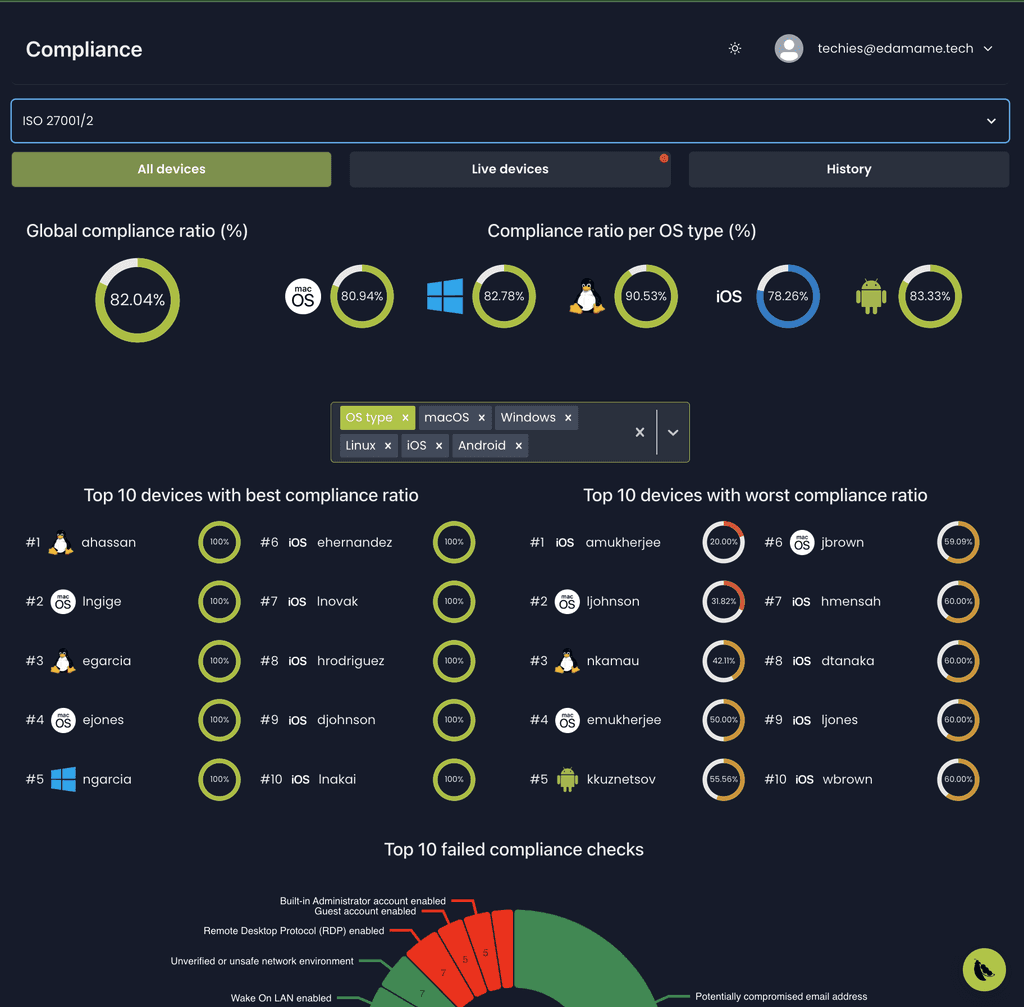
Endpoint compliance
Verify compliance of endpoints company-wide using standards like ISO 27001, PCI DSS, SOC 2, and more.
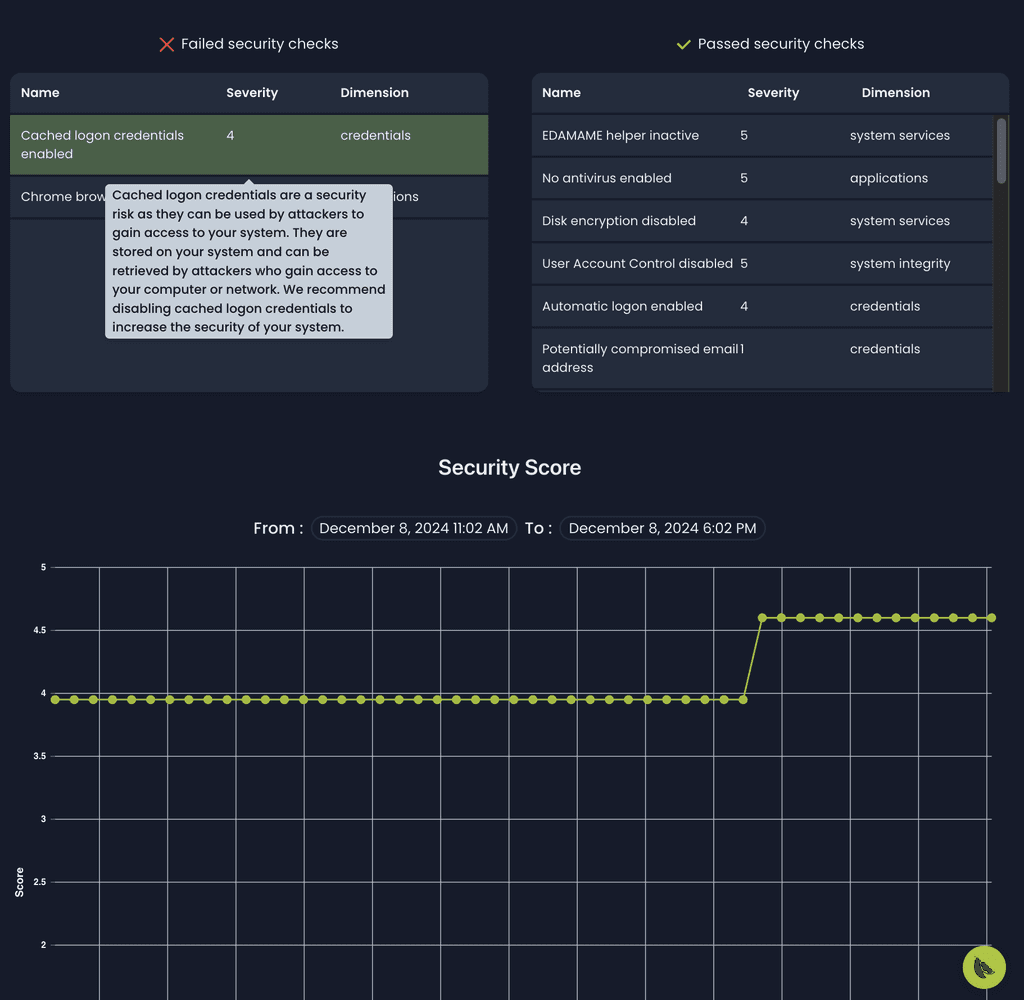
Collaborate with users to help them uplevel their security posture while fully preserving their confidentiality.
Device security troubleshooting
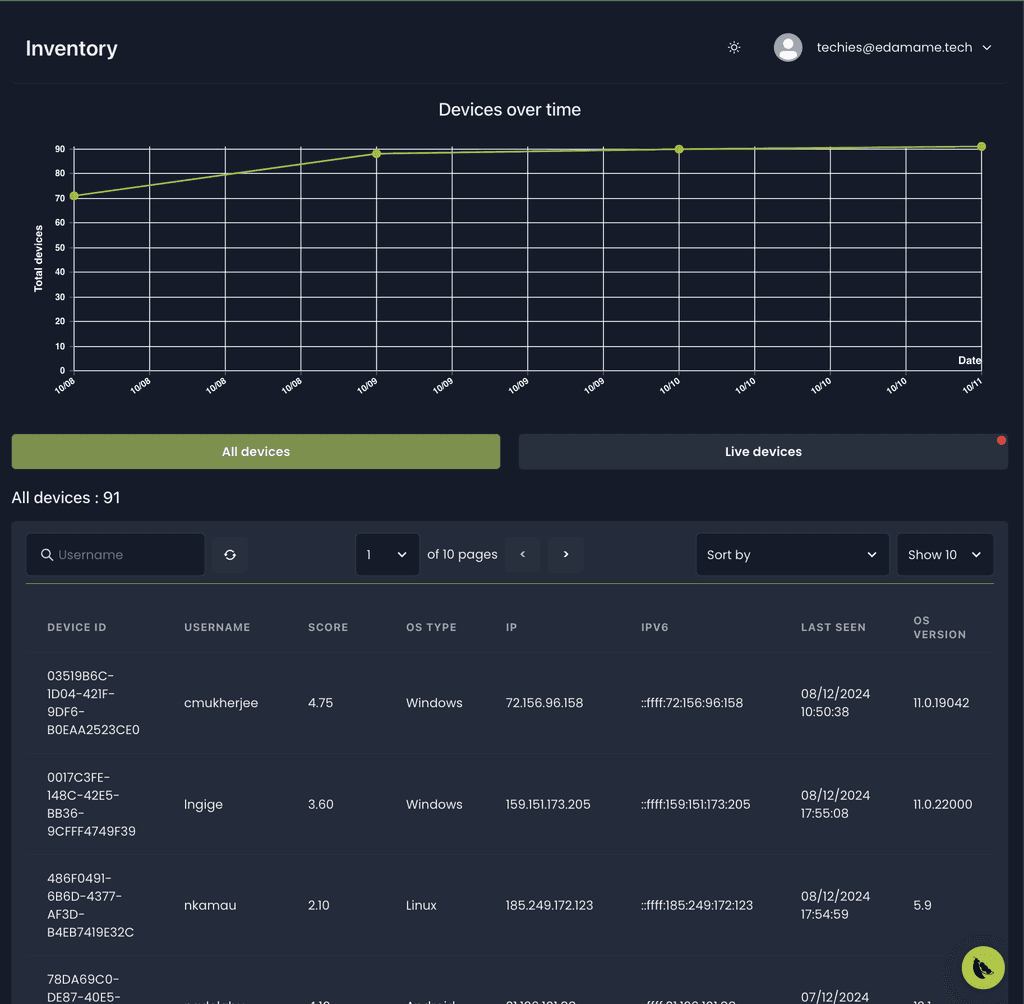
Device inventory
Explore endpoints -- laptops, phones, tablets, CI/CD runners, coding agents, and test machines -- in your SDLC and identify those requiring attention.
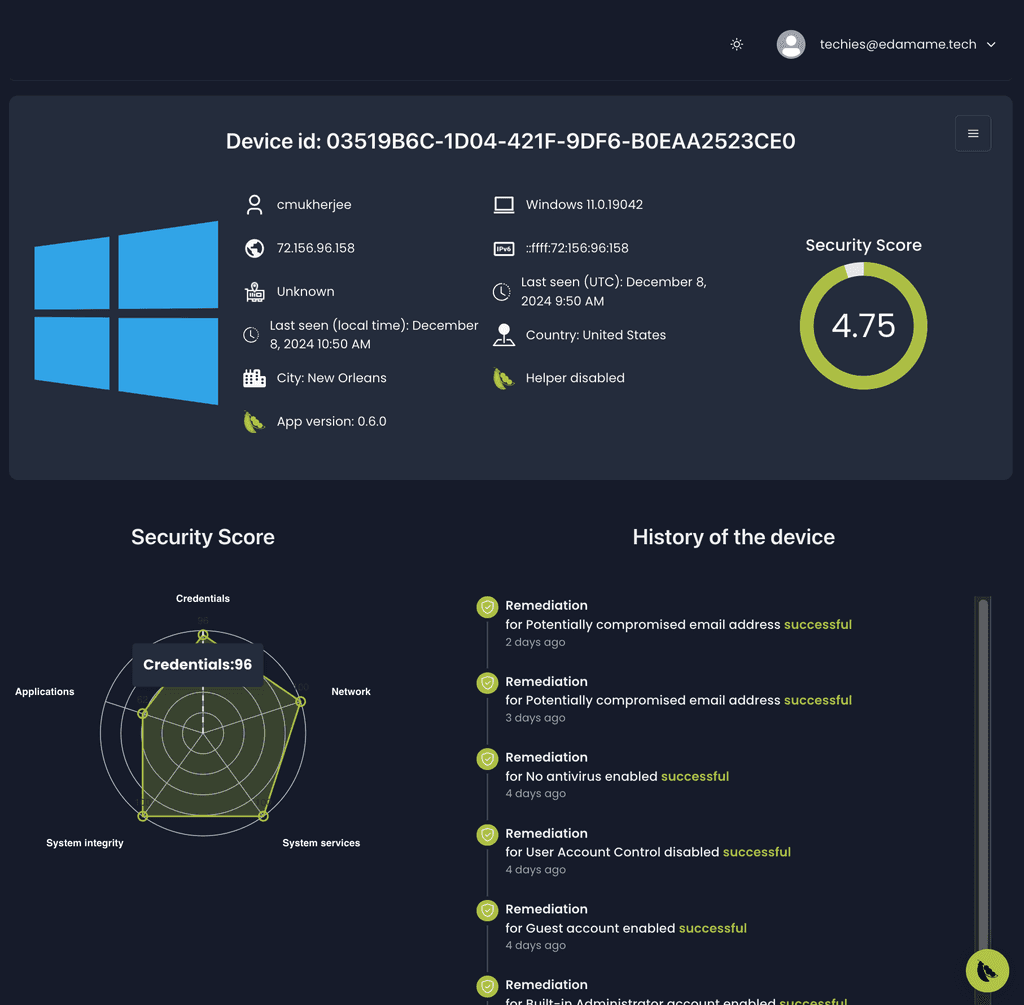
Endpoint security posture
Gather holistic insights and events on the SDLC security posture covering all endpoints accessing critical code, secrets, or sensitive data.
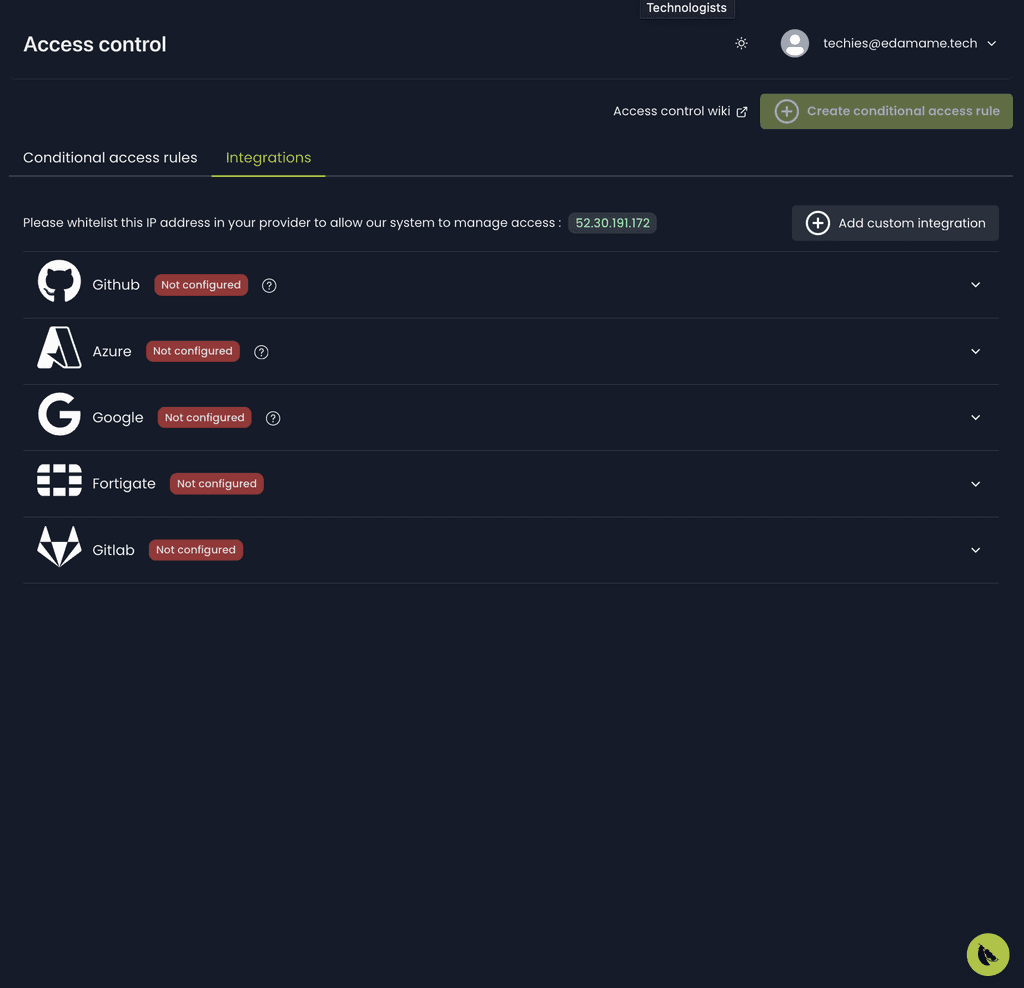
Device-based access control
Integrate with conditional access solutions, granting or denying access to resources based on the security posture of the device.
Zero Trust
Secure any SDLC environment with EDAMAME. Seamlessly integrate with source control using a Zero Trust approach with Identity Providers, native access control, and network-based access control. EDAMAME Hub gives you posture-based access and audit-ready visibility across environments—without remote device control.
Zero Trust

Manifesto
Our Manifesto for Tech Leaders: User-up Security elevates your SDLC
By 2025, decentralized cybersecurity won’t be a choice—it will be a necessity. To keep pace, organizations must evolve from rigid, admin-down control to an empowered model where teams can respond instantly at the point of action. EDAMAME makes this shift possible, giving technology leaders a way to share SDLC security responsibility with developers while maintaining full visibility and strategic oversight.
Security Without Undermining Productivity
EDAMAME hardens what matters without removing admin rights or forcing VDI. The AI assistant provides contextual guidance and one‑click fixes, so dev velocity stays high while risk stays low.
Security Beyond Compliance
Move from quarterly checklists to continuous posture. Device‑side audits, network scanning, and AI/ML traffic analysis surface issues early; signed reports map to SOC/ISO expectations when you need them.
No Admin Abuse, Ideal for Contractors
Your legal and privacy posture matters. EDAMAME is reporting‑only—no remote wipe, no covert changes. Contractors and partners stay cooperative because we verify outcomes (posture), not seize control.
Zero Trust Integration
EDAMAME integrates Identity Providers, repos, VPNs and network devices to enforce conditional access. Only secure, recognized endpoints and monitored coding agents can access critical resources. Agent behavior is correlated against declared intent through MCP, aligning with zero-trust principles at the runtime layer.
Versatile for CI/CD, Coding Agents and Dev Machines
One product language across laptops, runners, and coding agent infrastructure. Same posture signals, same attestations, same access rules -- less policy drift, more clarity.
Trusted by developers, open-core
Open‑core and developer‑first. The assistant speaks plain language; developers fix locally and learn along the way. Culture shifts from avoidance to practice.
Compliance
EDAMAME integrates seamlessly with compliance automation frameworks by exporting real-time device security assessments to third-party platforms like Vanta. Its unique approach makes it ideal for both company-owned and personal devices. Organizations can feed continuous device posture data into their compliance workflows, enhancing visibility and control. This integration supports frameworks such as SOC 2 and ISO 27001, streamlining evidence collection and audit readiness.
Testimonials
We understand the delicate balance between enabling innovation and maintaining robust security. These testimonials reinforce our commitment to empowering organizations with solutions that enhance security without compromising productivity or agility.