
Devs
Understand, Strengthen and Prove Your Device’s Security and Privacy
Meet your AI security assistant. EDAMAME explains what’s risky on your machine, why it matters, and how to fix it right now—without breaking your tools or taking your admin rights. Generate signed posture proof when clients or teams ask.
Manifesto
Our Manifesto for Developers: You are the future of SDLC Security
At EDAMAME, we believe that developers are the cornerstone of SDLC Endpoint Security. Our goal is to empower you to build secure, resilient software without compromising your creativity or productivity.
Features
Transform Your Security Workflow
Understand the security posture of your laptop or tablet and take an active role in your own protection. With EDAMAME Security, you don’t just see the risks—you’re guided by an AI assistant toward smart, automated fixes that reduce them. Gain the knowledge and confidence to secure your device against digital threats, align with the toughest enterprise standards, and do it all without compromising your privacy.
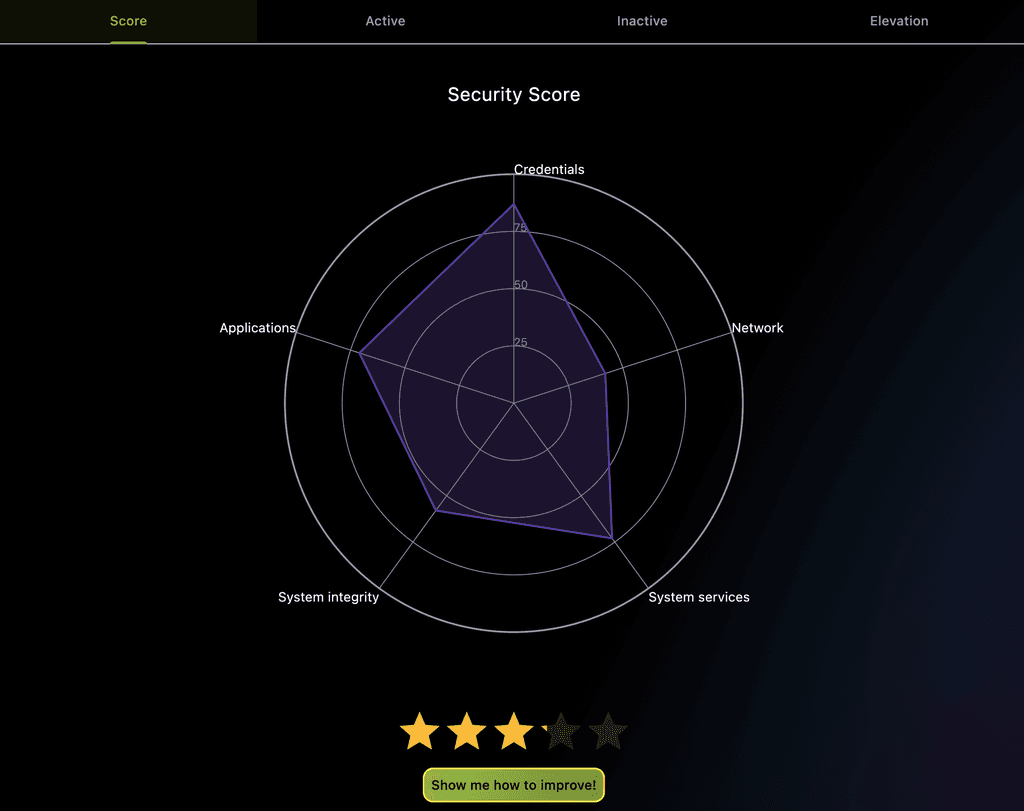
Automated Audits and Hardening
Continuous checks against OS best practices; guided remediations (enable firewall, harden services, apply patch) with user‑approved changes.
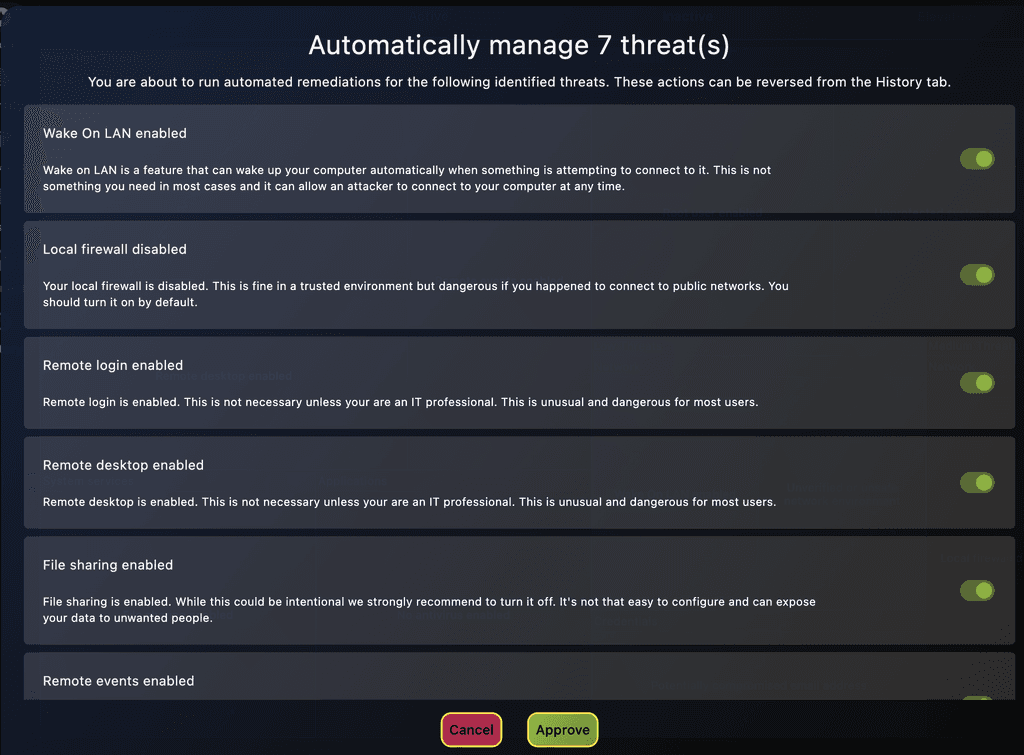
Produce Signed Compliance Reports
Click to produce ISO/SOC‑aligned posture reports for clients and security teams. Proof over promises.
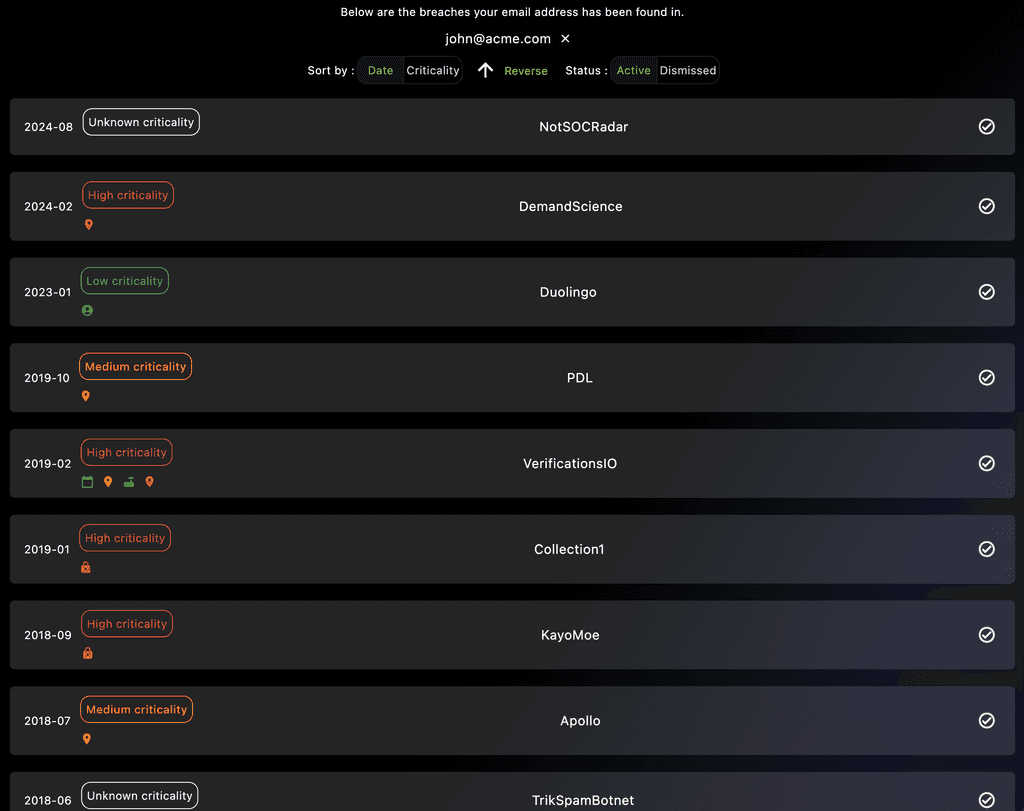
AI-Enhanced Identity Breach Management
Verify if your credentials have been compromised and receive AI-driven assistance. Stay proactive with insights into data breaches affecting your email addresses.
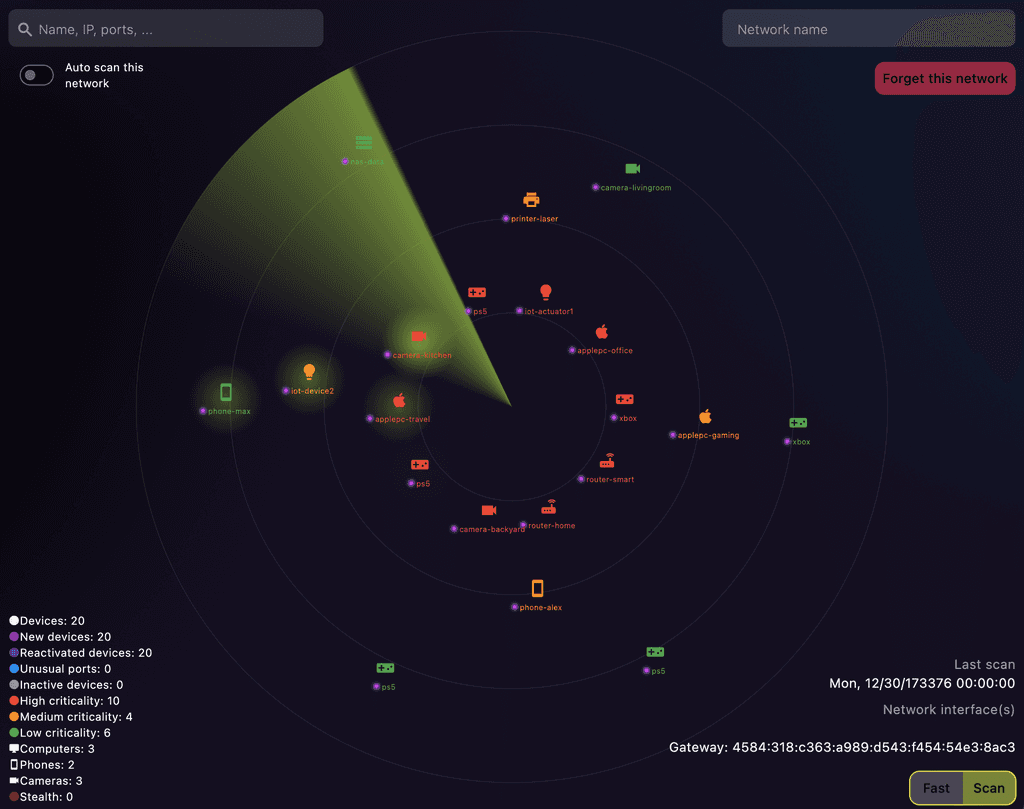
Advanced Network Scanning with AI Analysis
Discover neighbors, find exposed services, and get plain‑language guidance to reduce your attack surface.
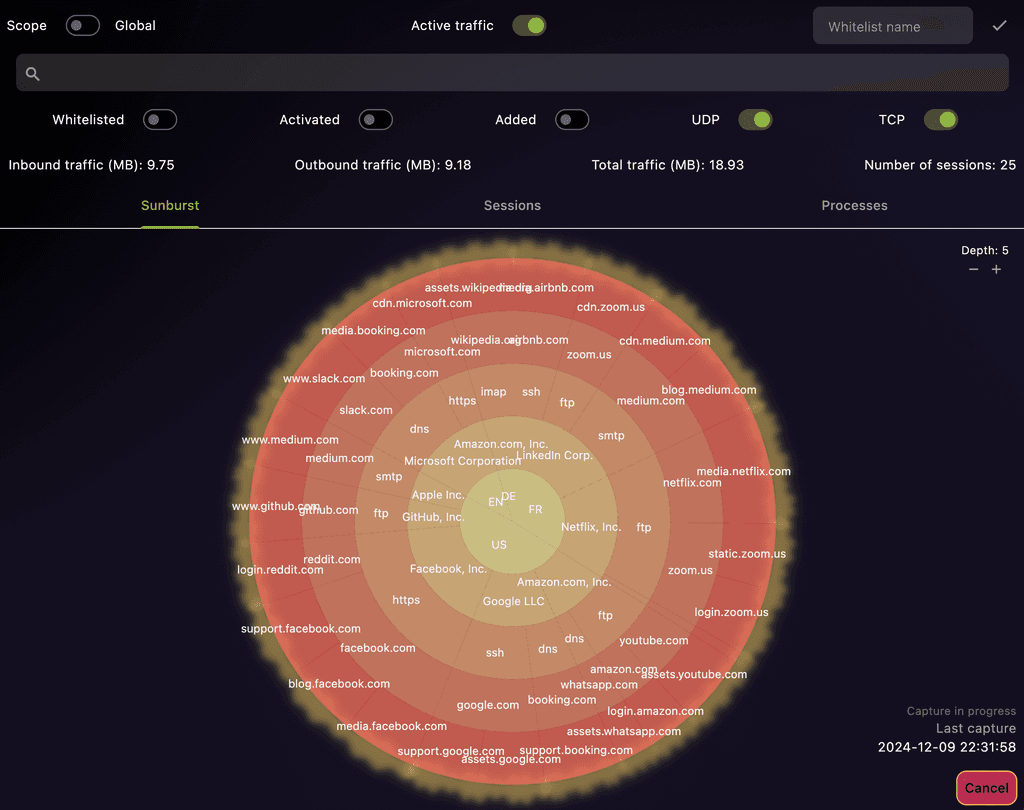
AI and ML based Process-Level Network Traffic Analysis
See which process talks to whom. ML flags anomalies; the AI explains potential risk and suggests next steps.
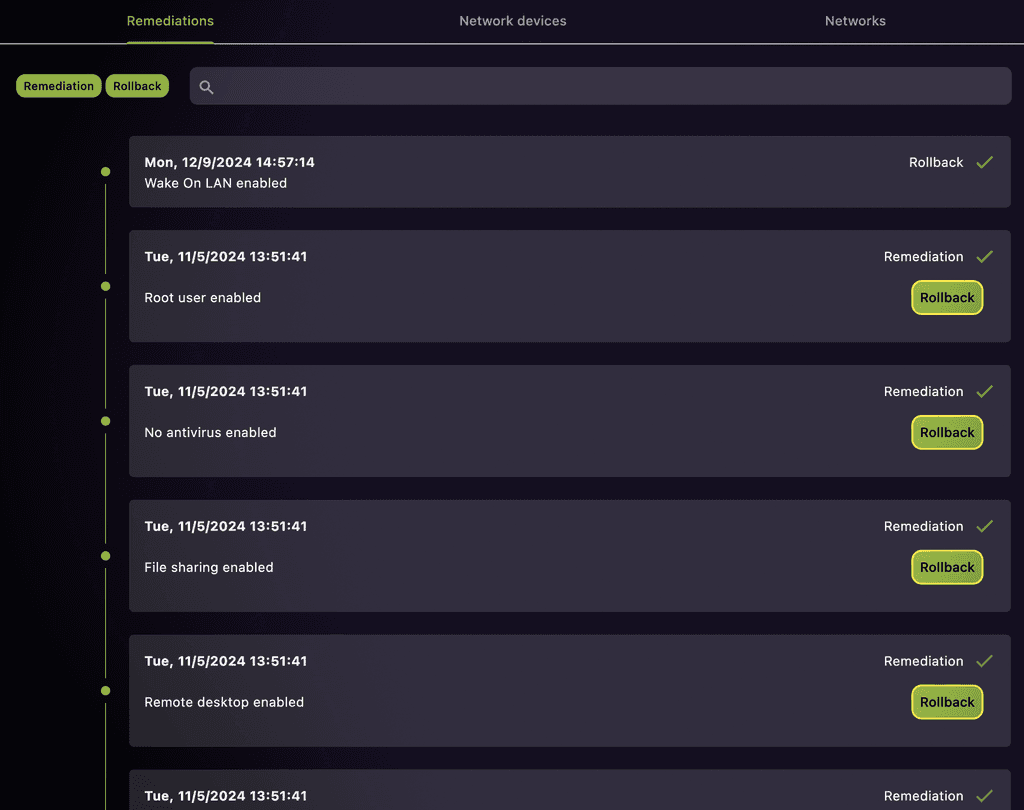
History and Rollback
Every change is tracked; revert safely if needed—you remain in control.
Who?
Who Is EDAMAME Security For?
Whether company‑held, contractor‑owned, or BYOD, EDAMAME helps you prove your device is safe—with an AI coach that keeps you compliant without slowing you down.
Testimonials
As developers, we know firsthand the struggle of balancing security with productivity. These testimonials validate our mission: building developer-first tools that protect without slowing you down—empowering innovation while strengthening security in the background.






