Coding Agents
Secure Your Coding Agents. From Server to Prompt.
Coding agents run with deep access to your systems. EDAMAME Posture gives you two integration paths: harden the server running the agent with the CLI, or let the agent monitor its own behavior through Model Context Protocol (MCP).
The Challenge
Coding Agents Are Powerful. And Exposed.
Coding agents like Cursor, Claude Code, and OpenClaw execute shell commands, access credentials, install packages, and modify system configurations autonomously. They are among the most privileged processes on your workstation or server. Their attack surface is specific and growing.
Two Modes
Two Integration Paths for Coding Agent Security
EDAMAME Posture offers two complementary approaches to secure your coding agents. Choose one or combine both for defense in depth.
Harden the Server Running Your Agent
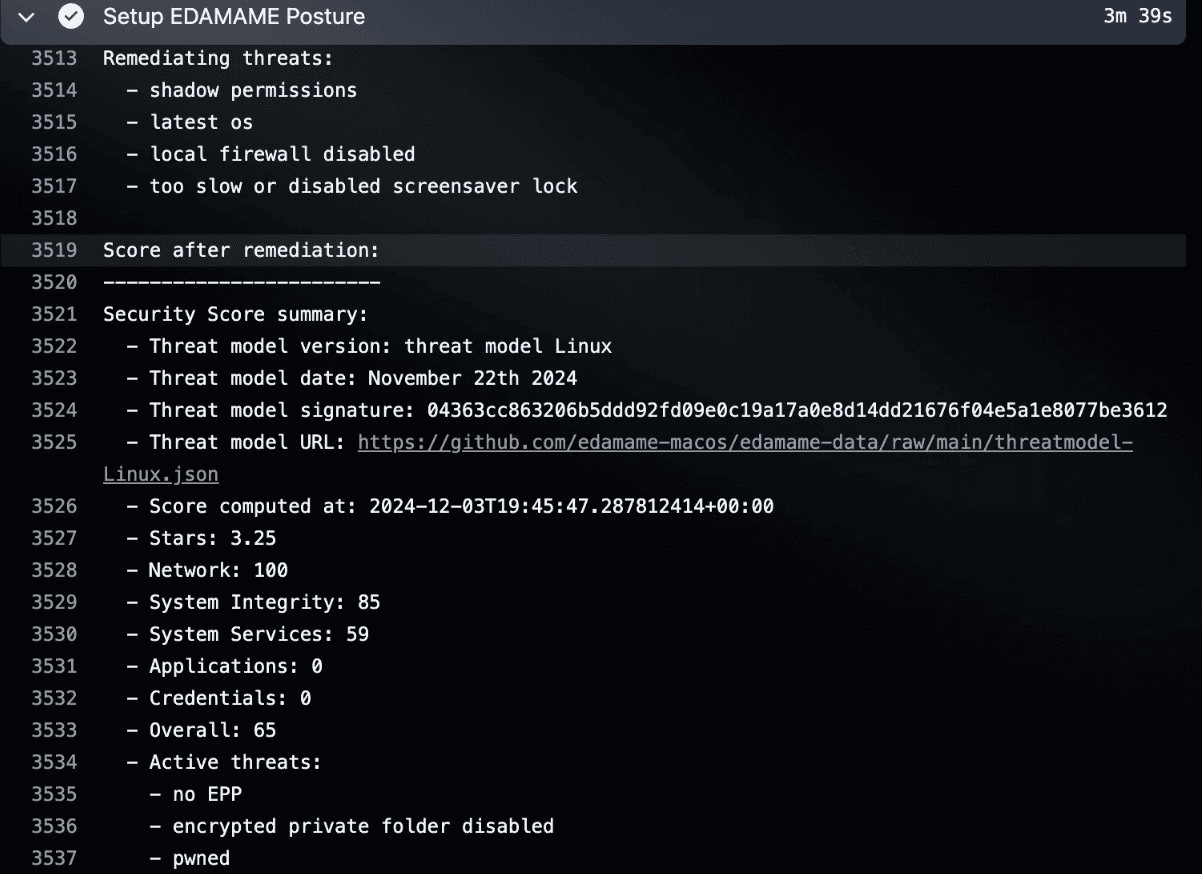
Deploy EDAMAME Posture CLI on the server or workstation hosting your coding agent -- the same way you would secure a self-hosted CI/CD runner.
• Continuous posture monitoring and scoring
• Automated hardening with agentic remediation
• L7 traffic analysis and LAN scanning
• Human-in-the-loop escalation via Slack
Let the Agent Watch Itself
Connect your coding agent to EDAMAME Posture via MCP. The agent queries real-time security signals and cross-references intent against actual system behavior.
• Two-plane security: reasoning vs. system truth
• Traffic divergence detection in real time
• Posture drift alerts with before/after evidence
• MCP integration for self-monitoring agents
Server Security
Harden the Server Running Your Agent
Deploy EDAMAME Posture CLI on the server or workstation hosting your coding agent -- the same way you would secure a self-hosted CI/CD runner. Continuous posture monitoring, automated hardening, and human-in-the-loop escalation via Slack keep the foundation secure while the agent works.
Agentic Security
Let the Agent Watch Itself
Connect your coding agent to EDAMAME Posture via MCP. The agent queries real-time security signals to cross-reference its declared intent against actual system behavior. When intent and reality diverge, the mismatch is the strongest early-warning signal.